Historically, the crypto market has moved in cycles and each bull swing has brought in newcomers to the space, attracted by headlines and word of mouth. This has naturally increased the prevalence of bad actors looking to take advantage of such newcomers through scams and other phishing schemes. These can result in a major loss of user funds who unknowingly take part in such schemes. Thus, at all times individual crypto users need to remain vigilant when operating in Yoroi and double-check information when conducting crypto transactions.
Private keys are protected through powerful encryption on Yoroi, which prevents attackers from directly stealing crypto assets. Therefore, if a user has not disclosed their seed phrase, ¹ these scams generally require the user to inadvertently sign a fraudulent transaction. Scammers have found success using social engineering to trick users into signing harmful transactions.
This is why self-custodial wallets – like Yoroi – are the first line of defense against these scams. It’s important to understand the nature of the attacks to spot them ahead of time, and never sign one of these malicious transactions.
In this blog, we’ll go over some of the most popular types of crypto scams that result in users unintentionally approving a fraudulent transaction and how to safeguard against them.
¹ For user security, Yoroi Wallet does NOT store seed phrases. Only the wallet owner has access to their seedphrase so it’s important to keep this phrase in a safe place.
1. Fake popular URLs
This scam is a modification of the classic phishing attack. In it, attackers create an identical-looking copy of a legitimate website and use that to lure unsuspecting victims. The fake site uses the same style, font, and branding as the original which can make it difficult to notice, even for experienced users.
Once a potential victim has entered the fraudulent site, a request opens in their crypto wallet and asks them to sign a transaction. This results in the user approving a transfer that drains the funds contained in his/her wallet.
2. Fake wallet apps and extensions
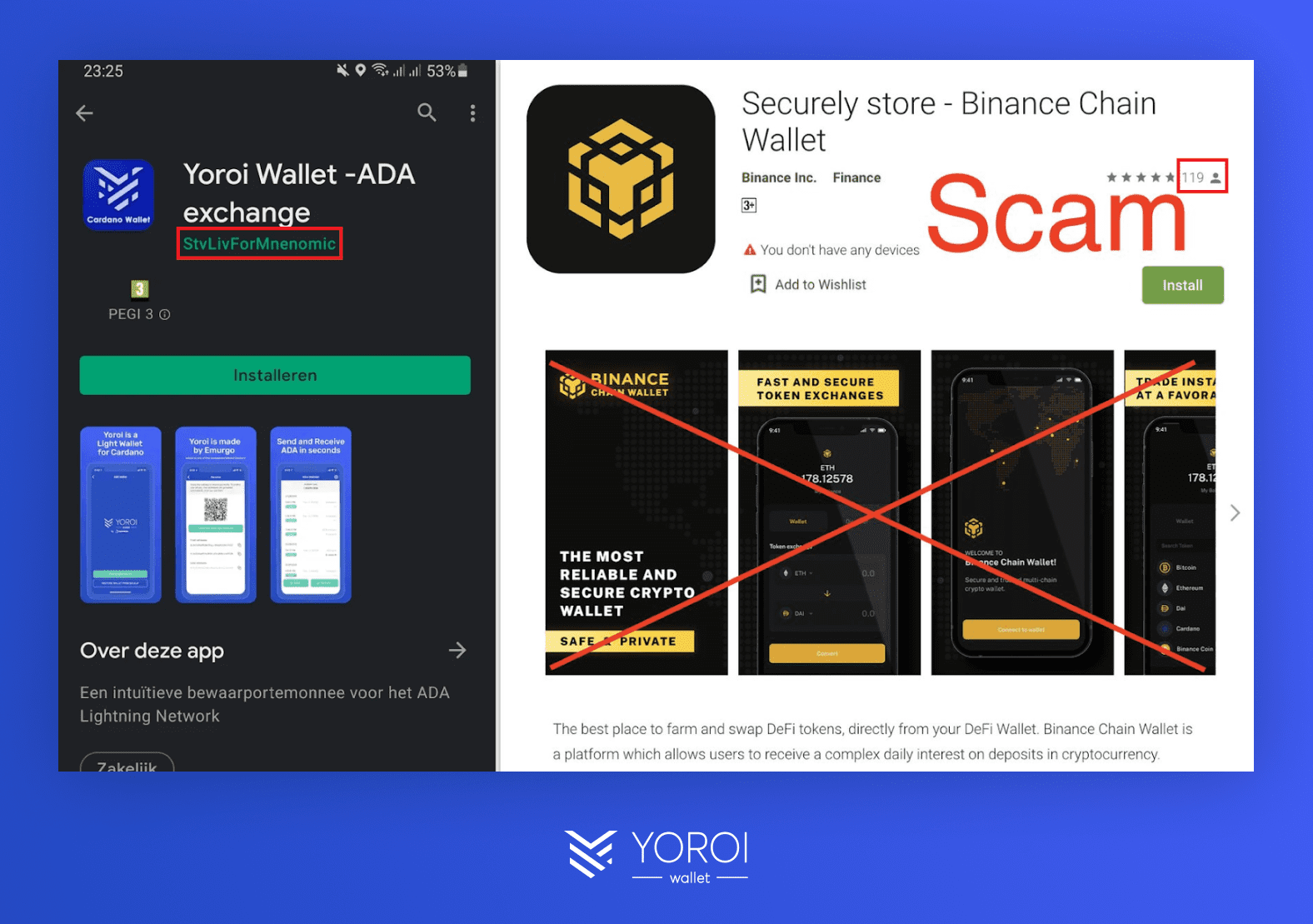
In the digital landscape of cryptocurrency, the emergence of fake wallets represents a pressing concern, especially within trusted marketplaces like the Chrome and Android app stores. These fraudulent entities cleverly masquerade as legitimate cryptocurrency wallets, leveraging the trust and credibility established by genuine projects.
By adopting the guise of authenticity, fake wallets entice unsuspecting users into a trap, prompting them to input sensitive information like seed phrases or to transfer their digital assets directly into the hands of scammers. This form of deception not only capitalizes on the enthusiasm surrounding cryptocurrencies but also exploits the inherent trust users place in app stores’ vetting processes, underscoring a significant vulnerability in the digital asset space.
3. Airdropped tokens or NFTs with links to fake sites

Another common type of crypto wallet scam or fraud consists of scammers sending new tokens and NFTs (non-fungible tokens) to targeted wallets to lure unsuspecting victims to a fake site. A user then discovers these new counterfeit assets in their wallet even though they haven’t bought these assets, which have arrived unsolicited. These NFTs and/or tokens, in their metadata, prompt the user to enter a website where they are typically promised lucrative offers to claim additional rewards, which are advertised to be free as part of a special promotion.
The unsuspecting user enters the website, which opens their browser-based crypto wallet claiming to be a transaction to mint new rewards for free. Instead, the user again is signing off their entire wallet balance to the attackers who created the fake sites.
Read more: What is an NFT and metadata?
4. Fake airdrops
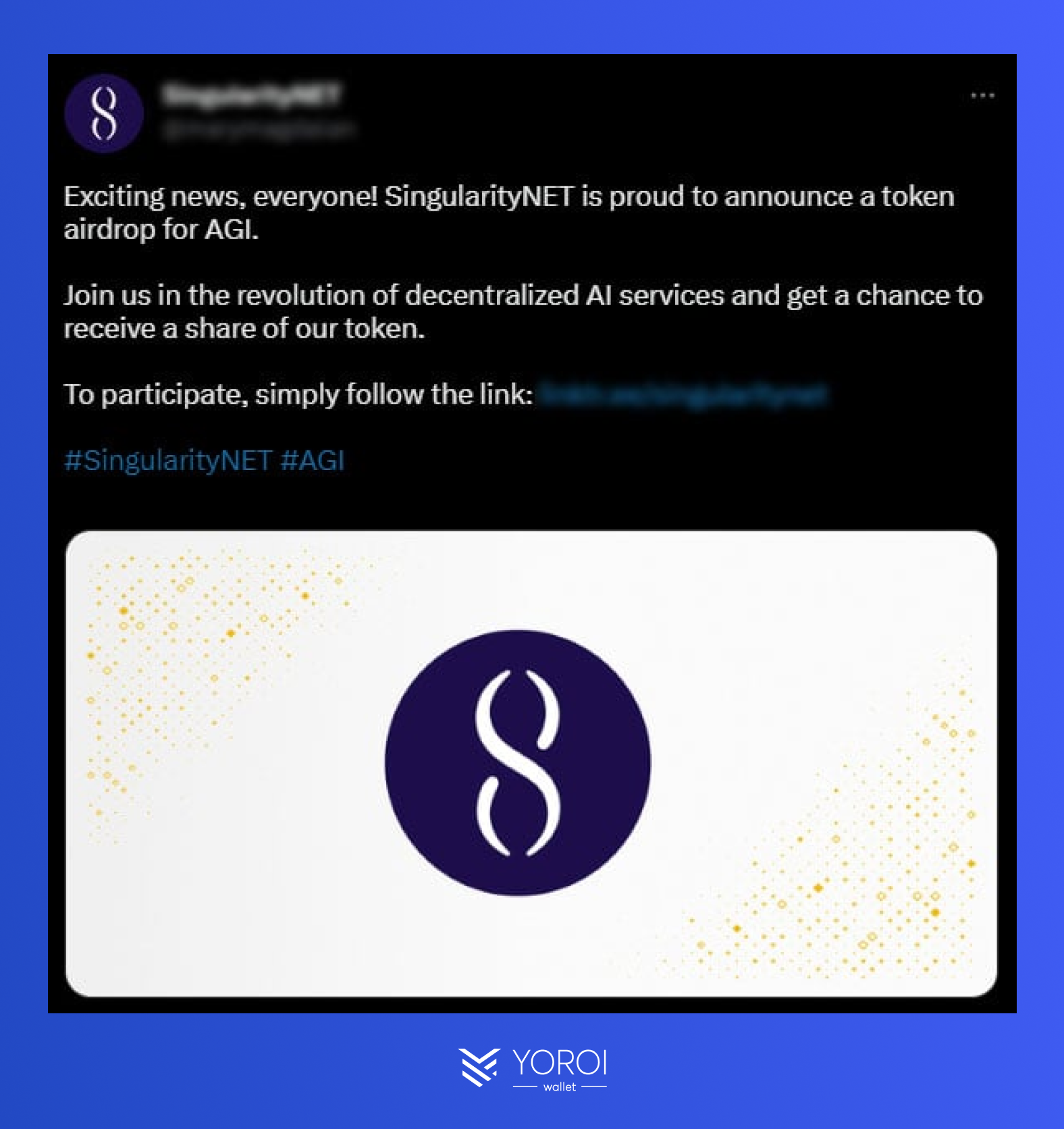
Airdrop scams are another type of common attack used by hackers in the crypto industry. Airdrops are promotions whereby a digital token or a cryptocurrency is automatically delivered to certain user wallets. On the surface, it would seem to users that they would be receiving crypto for free. Airdrop scams use social engineering to exploit the willingness of crypto users to participate in incentivization programs to open their wallets and create a transaction that drains their funds.
For this type of crypto scam, the attackers pose as a legitimate protocol or influencer, promoting a fake airdrop portal that requests users to connect their wallets on a website. The sites are always very well constructed and seem official. Sometimes, these sites may request the seed phrase of a user’s wallet. If not, they ask to sign a transaction that claims to be an airdrop when, in fact, it drains the user’s crypto wallet of all its assets.
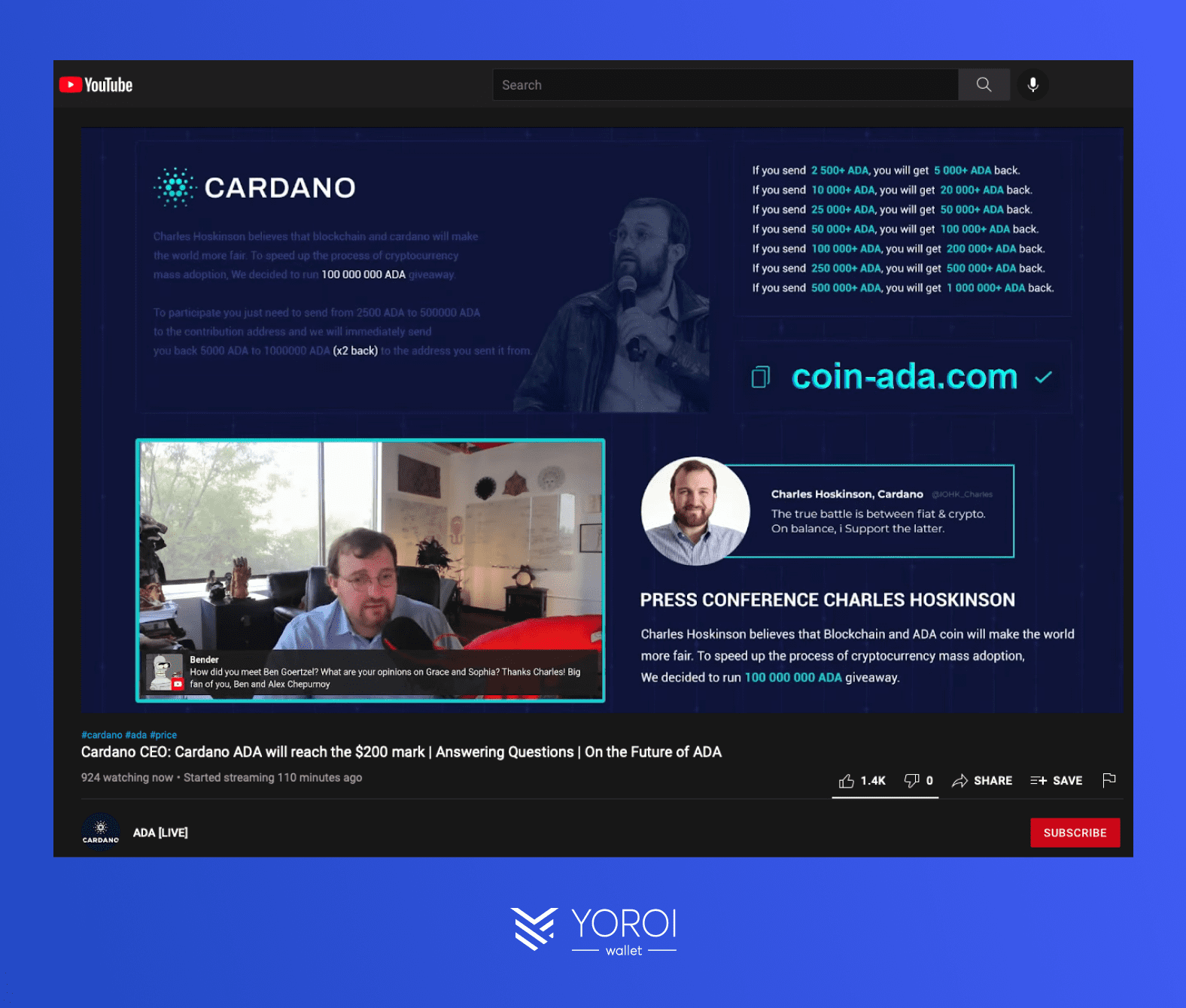
These types of scams are propagated on all forms of social media, email, and text messaging – including YouTube.
- Look for misspellings or slight variations in domain names
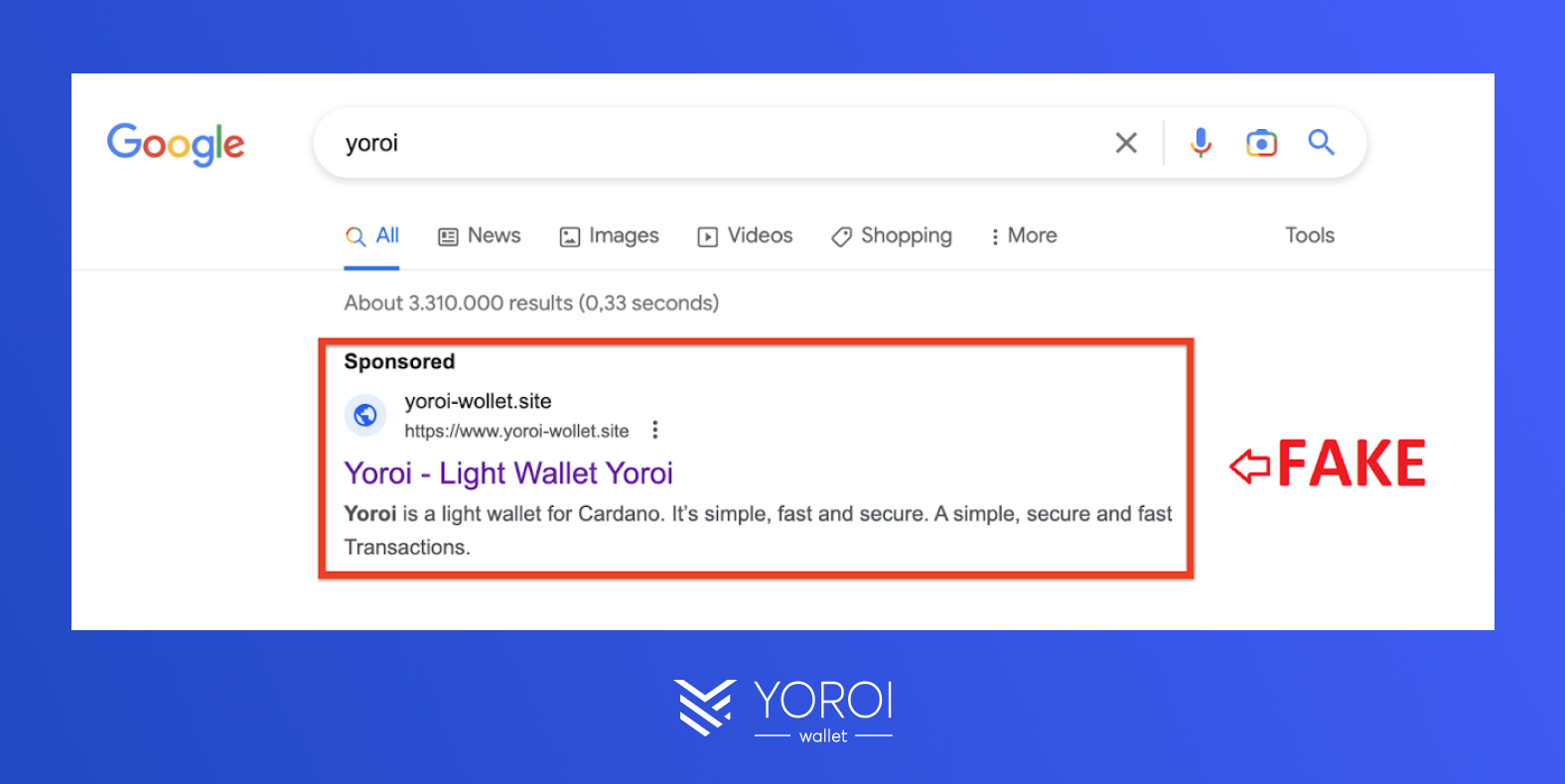
A website’s name is often purchased on a domain name service. This means the name is reserved for the person or organization who bought that particular word or combination of words. Attackers often use very similar names but with slight variations in the actual spelling of the domain.
Another common tactic is to buy the same domain name but use a different extension. For example, if the domain name is under an extension .com, attackers will buy the same name but with an extension .org, .io, .site, or any other valid extension on the market.
The official website for Yoroi Wallet is https://yoroi-wallet.com.
- Check for secure connections (https://)

Legitimate projects and products usually always buy the security certificate for their website. When you go to a site that uses HTTPS (connection security), the website’s server uses a certificate to prove the website’s identity to commonly used internet browsers such as Brave, Chrome, Opera, Edge, etc.
This gives some added measure of security that the site is the correct one.
Yet, an SSL certificate by itself is not enough to ensure the authenticity of a site.
It’s a good first line of defense, but other verification methods are also needed as all good scams use SSL certificates. If a website does not have an SSL certificate, that may be a cause for concern, but having an SSL certificate should not inspire confidence on its own.
- Be wary of unsolicited messages
Attackers often contact crypto users on popular social media applications such as X, Reddit, Telegram, Discord, and others with promotions to airdrops, giveaways, general investment opportunities, and other “too good to be true” campaigns. Any unsolicited message should be viewed with caution and suspicion. Never give any personal information to people who randomly message to engage and never click on any unverified link provided in those messages.
- Asks for a user’s private key, seed phrase, or other sensitive information
The seed phrase is the master key of any crypto wallet. A dApp will never ask for the seed phrase of a wallet to work, as it only needs the user’s signature on a transaction. Therefore, always leave any site asking for this information.
- Download wallets exclusively from official sources
The battle against such scams necessitates a dual approach, combining user vigilance with community-driven education.
For users, it is imperative to download wallets exclusively from verified, official sources. This cannot be overstated, acting as the first line of defense against fraudulent schemes.
Moreover, the open-source nature of projects like Yoroi Wallet offers an additional layer of security, allowing the community to inspect, audit, and verify the integrity of the software they’re entrusting with their assets. This culture of transparency and self-custody is emblematic of the broader Cardano ecosystem’s ethos, which champions decentralization and user empowerment.
As the crypto community continues to navigate these challenges, fostering an environment of awareness and skepticism towards unverified sources becomes crucial in safeguarding digital assets against the threat of fake wallets.
Some tips to avoid downloading a fake wallet:
- Always go directly to the developer’s official website for the proper download links/
- Double-check the App Store details.
Also, before installing the app, review the publication on the store and ask yourself:
- Does it have an adequate number of reviews?
- Who is the developer?
- Are there multiple versions of the same app?
- Are there spelling errors or poor grammar?
- Verifying website authenticity
As stated before, attackers use slightly different spelling or a different extension to lure victims to a fake website. For this reason, never click on a link provided on a message, tweet, post on a message board, email, or any sort of public forum.
If a crypto product or dApp has caught your attention, look for URLs found through official sources. Verify the URL with the project’s official channels (more than one), join the community, and read some of the messages to verify they are talking about the project as explained. There is no method to 100% proof check projects, especially if they are small or have been around for a short period.
Here, the best advice we can provide is to have a secondary wallet, one that holds minimal funds, or better yet, no funds. That way, when a site asks to sign a suspicious transaction, no crypto assets are at risk.
- A very strong sense of urgency
Stop and carefully review any transaction before it’s signed by your wallet. This is the last stop before any change is made to the balance of a crypto account so there is no need to rush. That is the main stopgap that prevents any sort of funds from being misallocated.
So, before signing a transaction always take your time to review the input required and the expected result. No one can move funds from a crypto wallet without the user’s signing on a transaction.
- Be wary of NFTs or tokens appearing in your wallet
If digital tokens or crypto magically pop up in your wallet’s balance that were not purchased directly, be very cautious with them. In some cases, projects do send tokens of NFTs to users for free to create buzz for a new service or platform.
Yet, this practice has been corrupted by attackers who instead use these assets to direct users to a scam website. If a token directs you to a website, don’t use the link provided. Instead, research the project, go through their socials, and see if the token is legitimate.
- Double-check URLs before entering any sensitive information
Never use a link or URL provided on a public forum or a third party. Either look for the name of the service on a search engine or from an official social media post. Always check the spelling of the site and also the extension used by the project.
- Use bookmarked or trusted links to access wallet services
After verifying the official site of a project, bookmark the address in a web browser. In the future, this will give direct and secure access to the same website without having to rely on links or other external references.
- Utilize browser extensions or tools that verify website authenticity
Many extensions can be found on the tools that check the authenticity of a site. These can give immediate warnings if the certificate of the site does not match the name of the URL, or worse, if the site has no certificate at all.
- Always double-check transactions before signing
Finally, always double-check the conditions of a transaction before signing. When interacting with smart contracts, the wallet will provide the address of the contract. Use it to compare it with the one posted by the project or ask in their social media channels to share the official smart contract address.
Developed by EMURGO Fintech, a division within EMURGO, Yoroi is an open-source crypto wallet for the Cardano ecosystem. Yoroi is also self-custodial, meaning the user has complete control over their Cardano ADA and can use it to stake and transact as preferred. To help users get the most out of their ADA, Yoroi gives access to all the different stake pools available in the Cardano community. Yoroi has been providing users with transparency, increased security, and decentralized collaborative innovation since 2018.
About Yoroi Wallet
- Yoroi Twitter: @YoroiWallet
- Official Website: yoroi-wallet.com
Disclaimer
You should not construe any such information or other material as legal, tax, investment, financial, or other advice. Nothing contained herein shall constitute a solicitation, recommendation, endorsement, or offer by EMURGO to invest.



